Agent¶
Overview¶
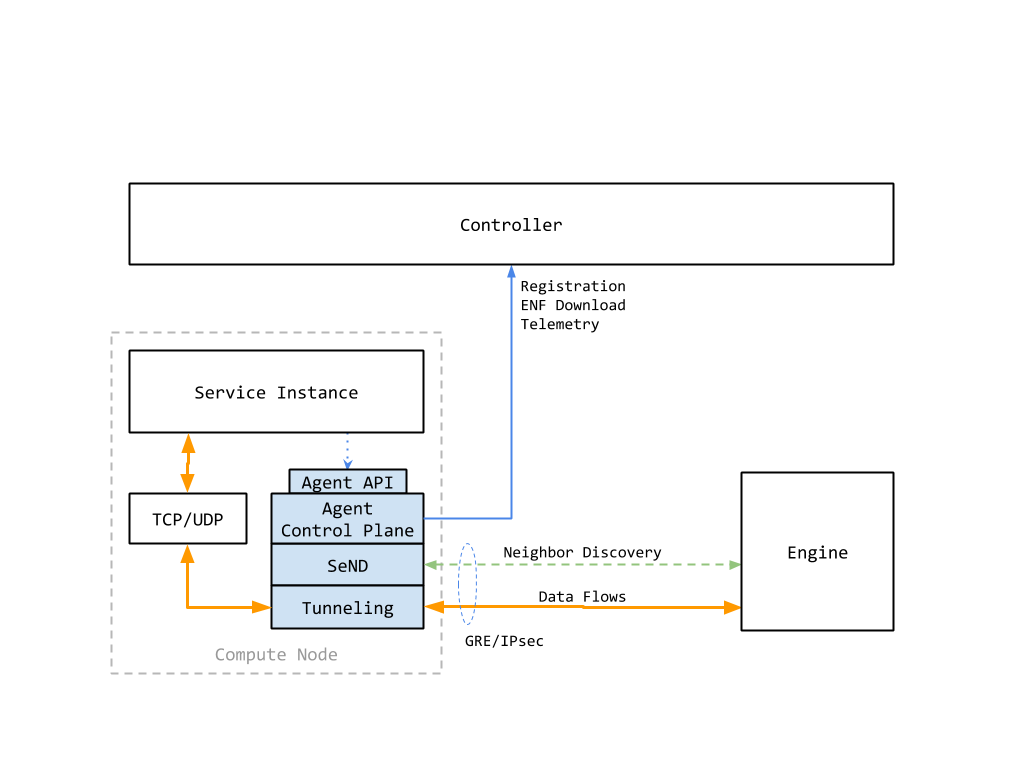
From a host operating system’s point of view, the Bayware Agent works on the layer 3 of OSI Model. The Agent receives IP packets on one IP interface, processes them and sends to another. Those all happen on data level. On control level, the Agent accesses controller’s RESTful interface to the applications located on the host.
The Bayware Agent is responsible for:
- node initialization
- node and link registration
- service endpoint registration
- service endpoint operation
The Bayware Agent comprises of:
- control plane module
- data plane module
Control Plane Module carries out such the functions: node initialization, node and link registration, service endpoint registration. Data Plane Module performs the service endpoint operation function.
Control Plane Module¶
Module Structure¶
Control Plane Module comprises of:
- RSA Key Generator
- CGA Address Generator and Validator
- Neighbor Discovery block
- Control Bayware Traffic Sender/Receiver
- In/Out ACL Management block
- Host and Link Registration/Keep-alive block
- HTTP RESTful Service block
- Service Endpoint Registration block
- Host Control Data
- Service Control Data
Control Plane Module implements such the interfaces:
- two-directional Bayware Data Plane interface
- client-side Controller SB interface
- server-side Agent RESTful interface
Module Logic¶
On its start the Bayware Agent loads its configuration and sets up the logging of its activity. As configuration parameters, the Agent accepts:
- host name (Full Qualified Domain Name)
- user name
- user password
- user domain
- controller name
At this stage the Agent verifies the self-signed certificate with the local host name in the certificate subject field. If needed, the Agent generates new keys and certificate as described later.
Next, the Agent starts REST server threads. From this point the agent is ready to process application requests.
In parallel, the agent requests a controller API gateway to provide initial configuration. The API gateway responses by redirecting the agent to the controller identity service for authentication. The Agent provides the identity service with the user name, password, and domain. As a result of successful authentication the agent obtains the token that enables agent access to the controller services. Using the token, the agent requests its own user profile with the scope description.
As a part of the scope the agent receives the netprefix. The Agent uses the netprefix to check or generate the host identifier–Cryptographically Generated Address (CGA)–as described later.
When the host identifier is ready, Control Plane module checks App and Net interfaces on operating system level. Thereafter, the Control Plane module starts Data Plane module. Now, Control Plane module is able to process SeND messages in its data plane thread, as well as Type I/II packets.
After start of Data Plane module, Control Plane module requests the controller to register this host.
Upon successful host registration, Control Plane module begin dispatching, via Data Plane module, the SeND advertisement packets using the previously generated RSA keys and CGA. At the same time, Control Module receives SeND advertisement packets from neighbors, via Data Plane module as well. When a new neighbor is discovered, Control Module initiates the connection establishment algorithm execution involving SeND exchange and controller’s API calls.
In parallel, Control Module monitors the host status and serves the application service requests. The module synchronizes its operational data with the controller, sending keep-alive messages periodically.
RSA and CGA Management¶
Control Plane Module is responsible for management of both RSA keys and CGA node identifier.
The RSA/CGA Management algorithm executions begins with hostname validation. The agent matches the actual host name against the name stored in the agent’s configuration file. If the names don’t match, the agent wipes out both RSA keys and CGA from its configuration file and generates a new RSA pair. The agent also generates a new RSA pair when the names match but RSA keys are not present in the agent configuration file.
When the pair of RSA keys are ready for use, the agent checks whether a CGA for this pair exists. If it doesn’t exist or CGA verification fails (i.e. CGA is not a derivative of public key and auxiliary parameters), the agent generates a new CGA. The CGA generation is performed as per RFC3972.
Data Plane Module¶
Data Plane Module can be logically divided into the following functional blocks:
- policy control block
- ingress and egress packet processing blocks
- control plane send and receive blocks
- application and network interface blocks
Policy Control Functions¶
Policy Control block allows to add or remove rules of packet processing. The block includes:
- Policy Control methods
- Egress Policy database
- Ingress Policy database
- Control Data database
Ingress and Egress Packet Processing Functions¶
Ingress and Egress Packet Processing blocks process packets in accordance with the policy. The blocks receive and transmit packets on the interfaces such as:
- application interface
- network interface
- interface with control module
Packets arriving from both local applications and the control module undergo the following processing steps:
- Egress policy is applied to the packet
- The packet payload is encrypted
- Optionally, IPv6 header is created or edited
- Optionally, TCP/UDP checksum is recalculated
- Ethernet header is created or edited
Packets arriving from both network and control module undergo the following processing steps:
- Ethernet header is removed
- Ingress policy is applied to the packet
- The packet payload is decrypted
- Optionally, IPv6 header is replaced or edited
- TCP/UDP checksum is recalculated
IPv6 ICMP packets proceed between control module and network interfaces without being processed inside data plane module.
Сontrol Plane send and receive functions¶
Data Plane module forwards packets between Control Plane module and network interface.
The packets from Control Module are sent to:
- Egress Policy applicator, if IPv6 SSM
- Net Egress Queue, if IPv6 ICMP
The packets to Control Module are received by Control Egress Queue from:
- Net Interface Listener, if IPv6 ICMP
- Ingress Policy applicator, if IPv6 SSM
Application and network interface functions¶
Data Plane module connects to Virtual TUN Interface for receiving and sending packets from/to local applications.
Data Plane module connects to Virtual GRE-TAP Interface for receiving and sending packets from/to network.